From being hunted to hunting the hunter
Data is everywhere and plentiful today. The cost of storage and memory has allowed us as a society to capture everything if we like it or not. With this bounty, including data from our network infrastructure from monitoring, cybersecurity professionals are using data to assist in the defense of their environments. For the longest time, cybersecurity professionals defended their networks reactively. Now, with big data, artificial intelligence, and machine learning, they are defending their networks proactively. Today, it is not a matter of if, but when your organization will be compromised. The goal is to prevent as many breaches as possible before they occur. So, let’s look at the latest advances in cybersecurity practices and tools that can move us from being the hunted to hunting the hunter.
With this bounty, including data from our network infrastructure from monitoring, cybersecurity professionals are using data to assist in the defense of their environments. For the longest time, cybersecurity professionals defended their networks reactively. Now, with big data, artificial intelligence, and machine learning, they are defending their networks proactively. Today, it is not a matter of if, but when your organization will be compromised. The goal is to prevent as many breaches as possible before they occur. So, let’s look at the latest advances in cybersecurity practices and tools that can move us from being the hunted to hunting the hunter.
In the beginning, cybersecurity professionals designed their networks using layering techniques throughout the network. Starting at the user’s devices, virus and malware scanners were used to defend against these threats. A local firewall prevented unwanted traffic from entering users’ devices. As you moved out to the perimeter of the network, you had a firewall installed to prevent unwanted traffic from entering your network. Businesses also created demilitarized zones (DMZs) to isolate public-facing servers from internal servers. But hackers got smarter, adapted their techniques and were able to penetrate networks with the best defenses in place through applications and users. Thus, there are application-layer firewalls that help with filtering out application-layer threats as much as possible. Also, businesses have used virtual private networks (VPNs) to connect remote users and sites to the internal network. In addition to these perimeter-type defenses, organizations installed monitoring devices such as intrusion detection (IDS) and intrusion prevention systems (IPS) to help alert and/or stop intrusions before they happen. Operating systems have the ability to monitor operating system traffic through different kinds of logging. Now, however, cybersecurity professionals have access to mounds and mounds of data to sift through. They need help to be able to find a needle in a haystack. This is where machine learning and artificial intelligence become valuable additions to a cybersecurity professionals’ toolkit.
Machine learning, the ability of systems to learn with data without programming, increasingly is being applied to cybersecurity tools. In the area of IDS/IPS, the ability of these systems to stop intrusions as they are happening is the goal. First step is to create machine learning models of normal traffic in a network, honing that model, and using it in IDS/IPS systems to stop abnormal network traffic as it is happening. The biggest issue with using machine learning in these systems are false positives, but that is improving.
Hence, this is allowing cyber defense to evolve from reactive to a more proactive approach. Lockheed Martin has created what is called the Cyber Kill Chain, which is a framework for the identification and prevention of cyber intrusion activities.
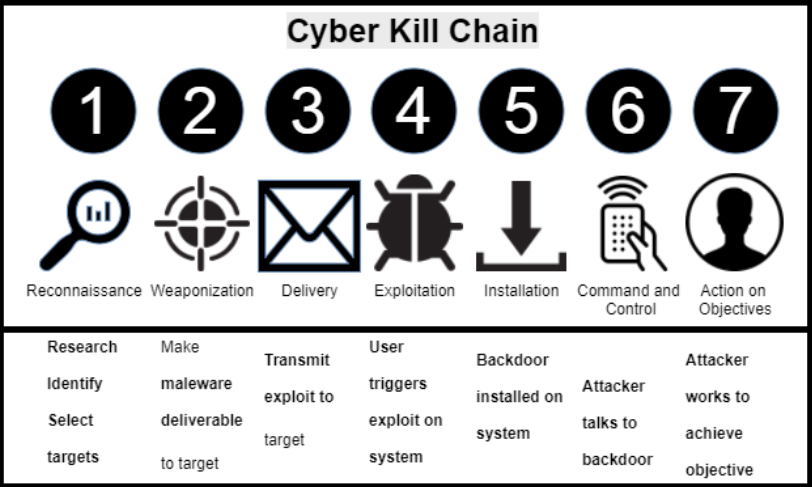
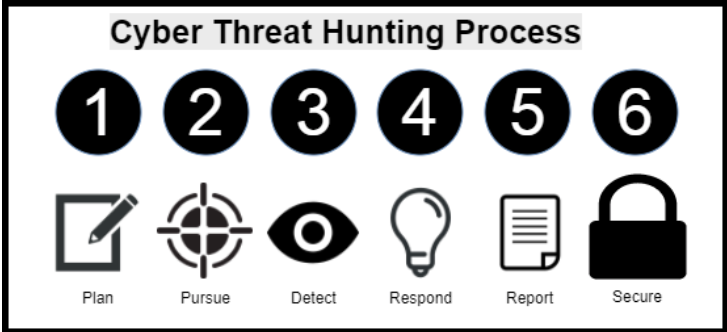
The goal is to intercept and eliminate cyber threats as early in the Cyber Kill Chain as possible. During the last several years, there has been a new role introduced in cybersecurity called Cyber Threat Hunting. The goal of Cyber Threat Hunting is to gain visibility of an organization’s vulnerabilities, detect threats early in the chain and improve its overall defense posture. The threat hunting project is a good resource for learning about different cyber threat hunting procedures being current employed. But, what does cyber threat hunting look like? Sqrrl has defined a threat hunting cycle as illustrated in the following graphic.
Big Data and data analytics techniques are being used to assist in this area. Artificial intelligence (AI) and machine learning are good at automating repetitive tasks, and recognizing and classifying patterns in data. With so much data for the cyber threat hunter to sift through, they are increasingly being used to assist. What’s more, there is a wide array of open source and commercial tools to assist a cyber-threat hunter today.
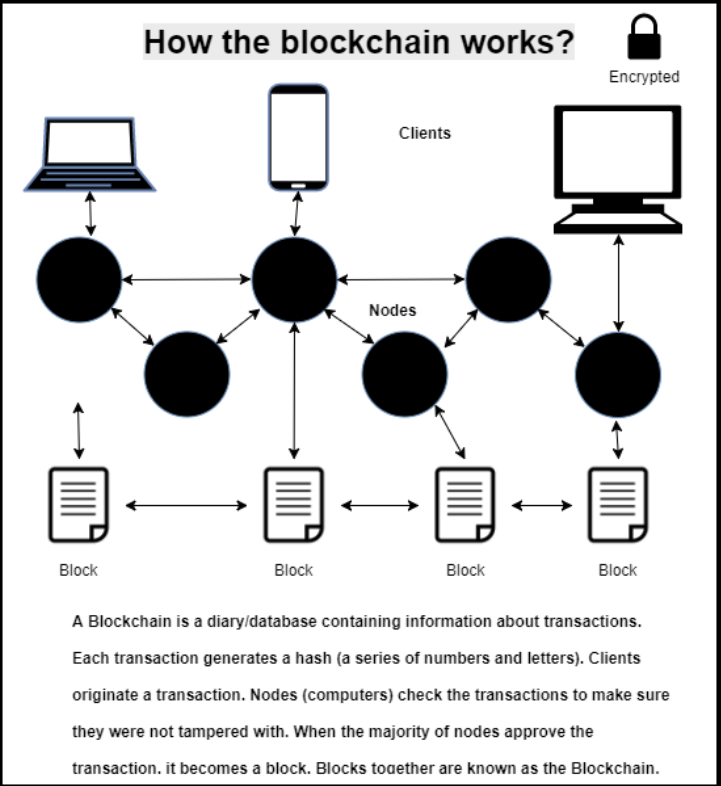
The latest technology that is emerging is Blockchain. Traditionally, blockchain enables secure transactions with cryptocurrencies such as Bitcoin and Ethereum in a distributed peer-to-peer computing environment. That same technology can be used to help prevent cyber-attacks through preventing identity theft, data tampering and potentially stopping denial of service attacks. Here’s how it works:
Now, let’s look at preventing identity theft. There are companies that are utilizing blockchain to protect identities through the blockchain-based Public Key Infrastructure (PKI). In this implementation, it acts as a distributed ledger of domains and their associated keys. There is no single point of failure. Traditional, PKI implementations rely on centralized authorities that we must be able to trust with our certificates. Blockchain removes the need for these centralized authorities since it handles this in a decentralized manner.
The next application of blockchain is in preventing data tampering. Since blockchain uses PKI, users can verify the data they’re handling. Also, there are companies that are creating decentralized storage using peer-to-peer computing techniques where data is stored on multiple peers and has algorithms to make sure the data is not corrupted. The data is encrypted throughout the whole storage and retrieval process.
The third application of the blockchain is in protecting the Internet’s critical infrastructure such as the Domain Name Service. A blockchain used in a distributed DNS system would never fail under extreme loads, thus removing distributed denial of service attacks from crippling the DNS system. There is currently a project exploring that.
Blockchain technology appears to be on the verge of revolutionizing the cybersecurity industry with new startups and approaches that will transform the way we look at cybersecurity in the future. And the future of cybersecurity does looks promising. For the longest time, cybersecurity was all about defending networks and recovering from breaches reactively. Now, with AI, machine learning and blockchain technologies, cybersecurity professionals will have more tools in their tool chest to protect and defend their organizations from cyber threats. Will we ever have 100 percent secure systems? Not likely. Cyber attackers will always find ways to penetrate defenses. The user is still, and will continue to be, the weakest link, so we will have to continue to educate our users on good cyber hygiene to help prevent cyber-attacks before they happen.
Keith A. Morneau is dean of Computer and Information Science at ECPI University. He can be reached at [email protected].
n